Public – Private Key Pairs & How they work
Public-private key encryption is used in many algorithms to protect important data. At the center of this unparalleled security model are public and private keys, two unique cryptographic keys that work together to guard digital interactions from prying eyes.
In this blog post, we will dive into how public and private keys relate to the end-to-end encryption model and how these keys enable secure communication, verify the authenticity of messages, and ensure that data remains confidential and unaltered throughout transmission. By understanding the intricacies of public and private key cryptography, you will realize how these tools can be leveraged to keep data secure, even in the face of persistent and evolving threats.
Public-Private Key Encryption Explained
Together, public and private keys help to ensure the security of the exchanged data in end-to-end encryption systems. A message encrypted with the public key cannot be decrypted without using the corresponding private key. This process is referred to as public-key cryptography or asymmetric encryption,
Public keys have been described by some as being like a business’ physical address – it’s public and anyone can look it up and share it widely. In asymmetric encryption, public keys can be shared with everyone in the system. Once the sender has the public key, he uses it to encrypt his message.
Each public key comes paired with a unique private key. Think of a private key as akin to the key to the front door of a business where only you have a copy. This defines the main difference between the two types of keys. The private key ensures only you can get through the front door. In the case of encrypted messages, you use this private key to decrypt messages.
What is Symmetric Encryption?
As opposed to asymmetric encryption, symmetric encryption is a cryptographic method in which the same key is used for both encrypting and decrypting the data.
Basic password protection can be seen as a form of symmetric encryption, where the same password is used to both encrypt and decrypt data. When a user creates a password for their account, it serves as the shared secret key for encrypting their sensitive information.
The Keys to Strong Security: How Public and Private Keys Relate to End-to-End Encryption
End-to-end encryption is a robust security model that ensures data privacy by encrypting messages and attachments on the sender’s device and decrypting them only on the recipient’s device – never on the server. This approach significantly reduces the vulnerability of exchanged data because there is no central point of attack, providing superior protection against unauthorized access and interception.
Public and private keys play a vital role in this secure communication process. The public key is used to encrypt the data, while the private key, which is securely stored on the recipient’s device, is used to decrypt the data.
This asymmetric encryption ensures that only the intended recipient can access and read the encrypted information, even if the data passes through unsecured networks. By using the public and private key pair, end-to-end encryption establishes a trusted and unbreakable channel for secure communication.
How Public-Private Key Cryptography Works
In public key cryptography, every public key matches only one private key. Together, they are used to encrypt and decrypt messages. If you encode a message using a person’s public key, they can only decode it using their corresponding private key.
Public and Private Key Encryption in Action
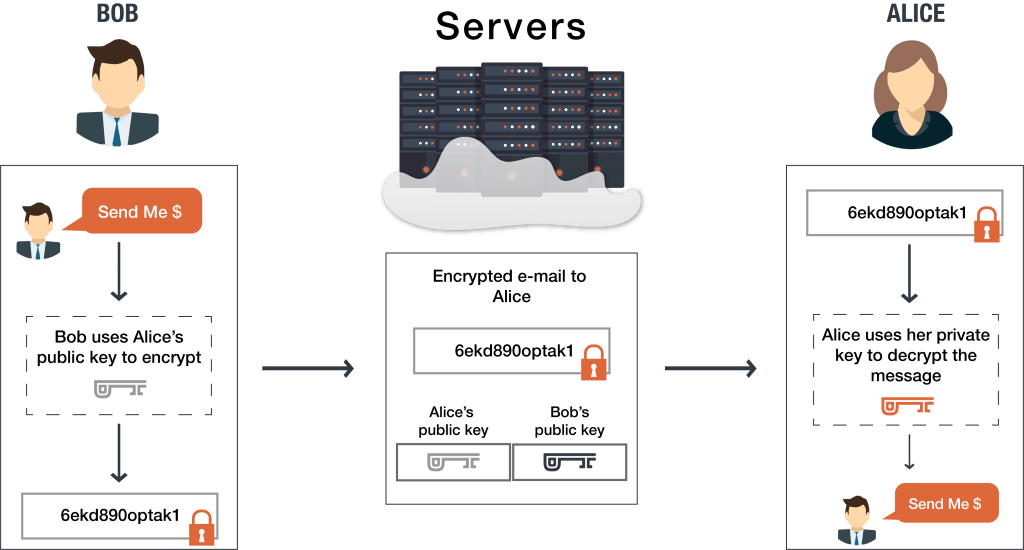
Bob wants to send Alice an encrypted email. To do this, Bob takes Alice’s public key and encrypts his message to her. When Alice receives the message, she uses the matching private key that is known only to her in order to decrypt the message from Bob.
Attackers might try to compromise the server in order to access the encrypted information, but they will be unable to because they lack the private key to decrypt the message. Alice is the only one who possesses the private key, and therefore is the only one able to successfully decrypt and access the message. When Alice wants to reply to Bob’s message, she simply repeats the process by encrypting her message to Bob using Bob’s public key.
Real-World Public and Private Key Encryption
1. Digital Signatures: Public and private keys can be used to create a digital signature, which assures that the person sending the message is who they claim to be.
Typically, the recipient’s public key is used to encrypt the data and the recipient then uses their private key to decrypt the data. However, with this form of messaging there is no way to authenticate the source of the message. Mike could get a hold of Alice’s public key (since it’s public) and send an end-to-end encrypted message to Alice while pretending to be Bob.
Using a digital signature security scheme, Alice would know not to trust the origin of the message unless the message is accompanied by a digital signature unique to the sender. In this case, Alice would look for Bob’s digital signature. If there is no digital signature to ensure that Bob is the sender, Alice can act with caution knowing that it could be anyone (like Mike, for example) sending the message under Bob’s name.
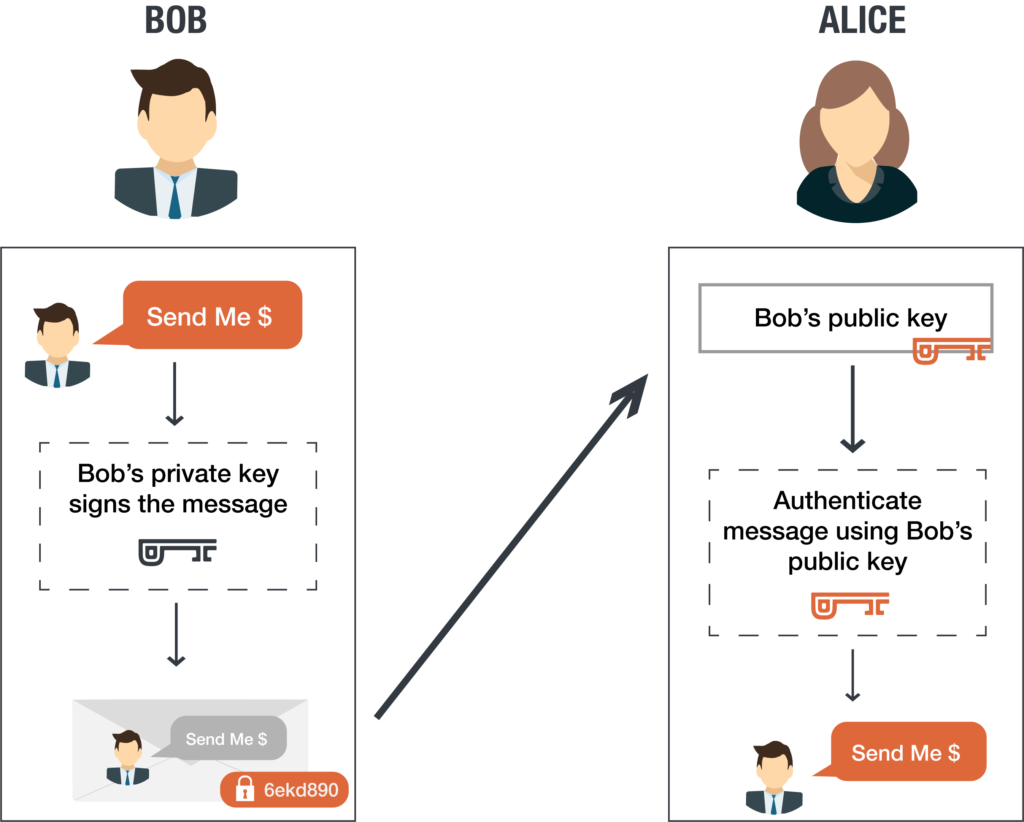
To create a digital signature, Bob digitally signs his email to Alice using his private key. When Alice receives the message from Bob, she can verify the digital signature on the message came from Bob by using his public key. As the digital signature uses Bob’s private key, Bob is the only person who can create the signature. If the digital signature is present and it matches Bob’s public key,, Alice can proceed with confidence that the sender is in fact Bob.
2. Diffie-Helman Key Exchange The Diffie Hellman key exchange demonstrates how users can securely exchange cryptographic keys over a public channel.
In the past, secure encrypted communication required that the individuals first exchange keys by a secure means such as paper key lists transported by a trusted courier. The Diffie–Hellman key exchange method allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure channel.
Unlocking the Process of Generating Public-Private Key Pairs
The public and private keys discussed here are not really keys at all, but rather large prime numbers that are mathematically related to one another. In this case, being “related” means that whatever is encrypted by the public key can only be decrypted by the related private key.
The private key cannot be guessed based on the public key. Because of this, a public key can be freely shared without threat of attack. The private key, in contrast, belongs to only one person.
There are several popular mathematical algorithms that are used to produce the public and private keys. Some well-respected algorithms include:
- Rivest-Shamir-Adelman (RSA): Oldest of the public-private key cryptography systems. Frequently used to transmit shared keys for symmetric key cryptography.
- Digital Signature Standard (DSS): A Federal Information Processing Standard specifying the algorithms that can be used to generate digital signatures used by NIST.
- Elliptic curve cryptography (ECC): As its name implies, ECC relies on elliptic curves to generate keys. It is offten used for key agreements and digital signatures. At PreVeil, we use elliptic-curve cryptography’s Curve-25519 and NIST P-256.
Benefits of Public-Private Key Encryption
By using a public and private key for encryption and decryption, recipients can be confident that the data is what the sender says it is and the sender is who they say they are. The recipient is assured of the confidentiality, integrity, and authenticity of data exchange.
Confidentiality is ensured because the content secured with the public key can only be decrypted with the private key, so that only the intended recipient access the information.
Integrity is ensured because the decryption process includes the step of checking that the received message matches the sent message. This validates that the message has not been changed in transit.
Authenticity is ensured because each message is digitally signed using the sender’s private key. The only way to decrypt that private key is with the corresponding public key, which the recipient can access. By signing the message with the sender’s private key, this guarantees for the recipient that the message really did come from the sender.
Public-Private Keys Decoded: Answers to Your Frequently Asked Questions
Question: Are public keys confidential?
Answer: No, public keys are not considered confidential. Unlike private keys, which must be kept secure and confidential, public keys are meant to be shared openly. Public keys are widely distributed as part of the public key infrastructure, allowing anyone to encrypt data or messages intended for the corresponding owner of the public key. While public keys are not confidential, they are a crucial component of asymmetric encryption. The combination of public and private keys forms the foundation for robust end-to-end encryption and safeguarding sensitive information from unauthorized access.
Question: Who can public keys be distributed to?
Answer: Public keys can be distributed to any authorized users who require secure communication. Authorized recipients use public keys to encrypt messages or data intended for a specific recipient. The distribution of public keys ensures that only intended recipients, with the corresponding private keys, can decrypt the data.
Question: What happens if someone obtains your public key?
Answer: If someone obtains your public key, there is generally no immediate risk to the security of your encrypted communications. Public keys are designed to be openly distributed and accessible without compromising data confidentiality. The strength of the encryption lies in the corresponding private key, which should remain secure and only accessible to you. Having your public key does not grant unauthorized access to your encrypted messages or data. The asymmetric encryption system ensures that only the holder of the private key can decrypt the information encrypted with the corresponding public key. Therefore, even if someone obtains your public key, they would still require the private key to decipher any encrypted communication or data. It is crucial, however, to safeguard your private key and implement robust security practices to maintain the integrity and confidentiality of your encrypted information.
Source: Orlee Berlove