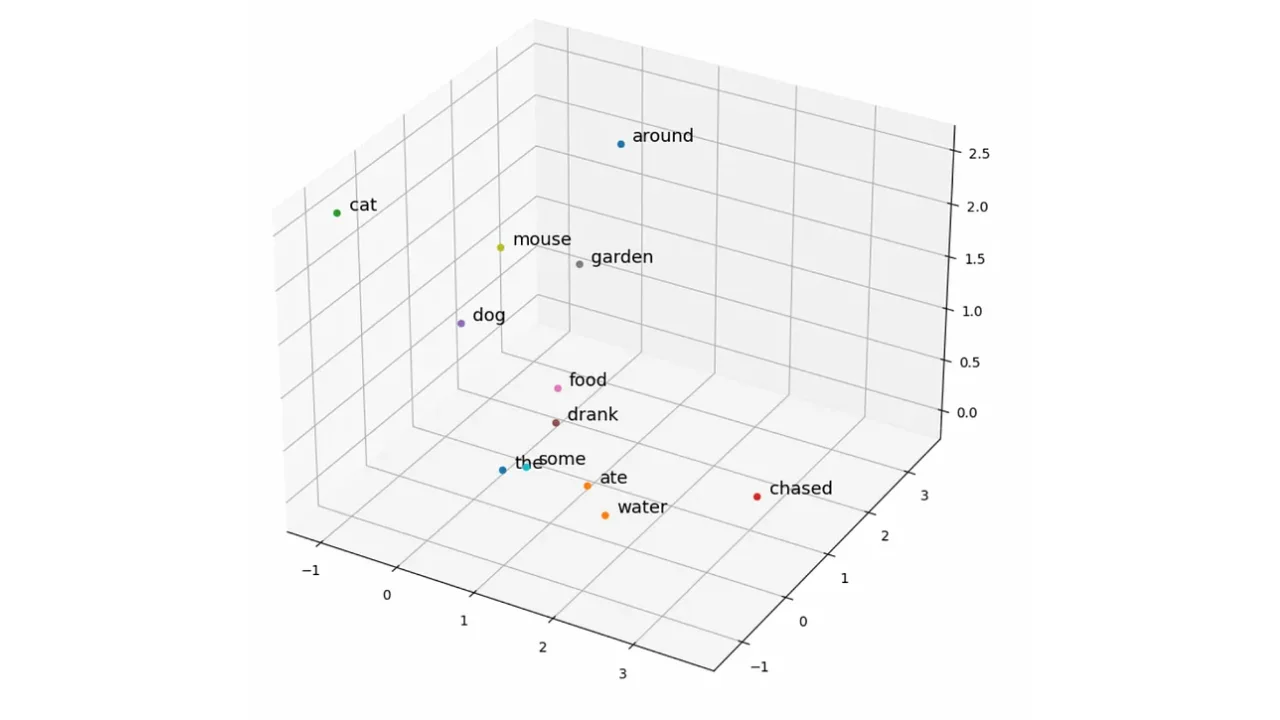
Word Embeddings with word2vec from Scratch in Python
Converting words into vectors with Python! Explaining Google’s word2vec models by building them from scratch. Part 2 in the "LLMs from Scratch" series - a complete guid
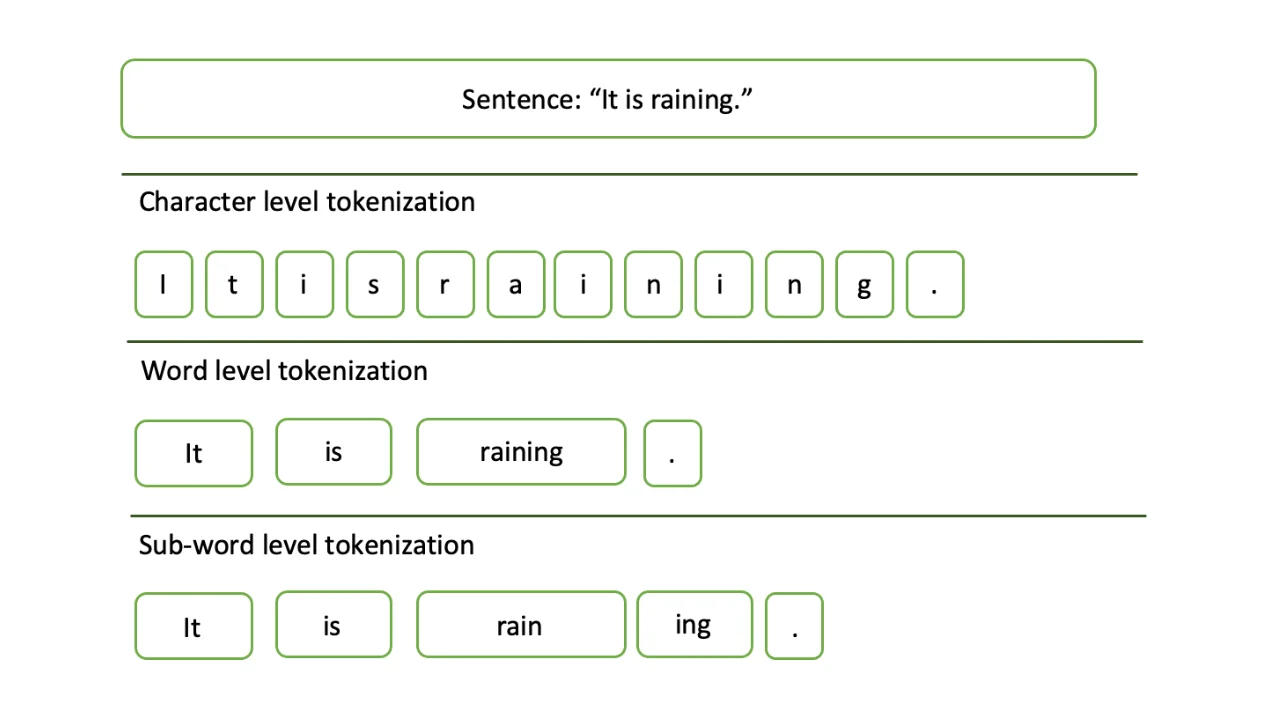
Tokenization – A Complete Guide
Large Language Models (LLMs) have become incredibly popular following the release of OpenAI’s ChatGPT in November 2022. Since then the use of these language models has exploded,
A Brief History of Large Language Models
Large Language Models (LLMs) have dominated discussions in machine learning for the past few years, and have transformed the landscape of AI for years to come. This article serves
AnythingLLM: The all-in-one AI app you were looking for
Chat with your docs, use AI Agents, hyper-configurable, multi-user, & no fustrating set up required. A full-stack application that enables you to turn any document, resource, o
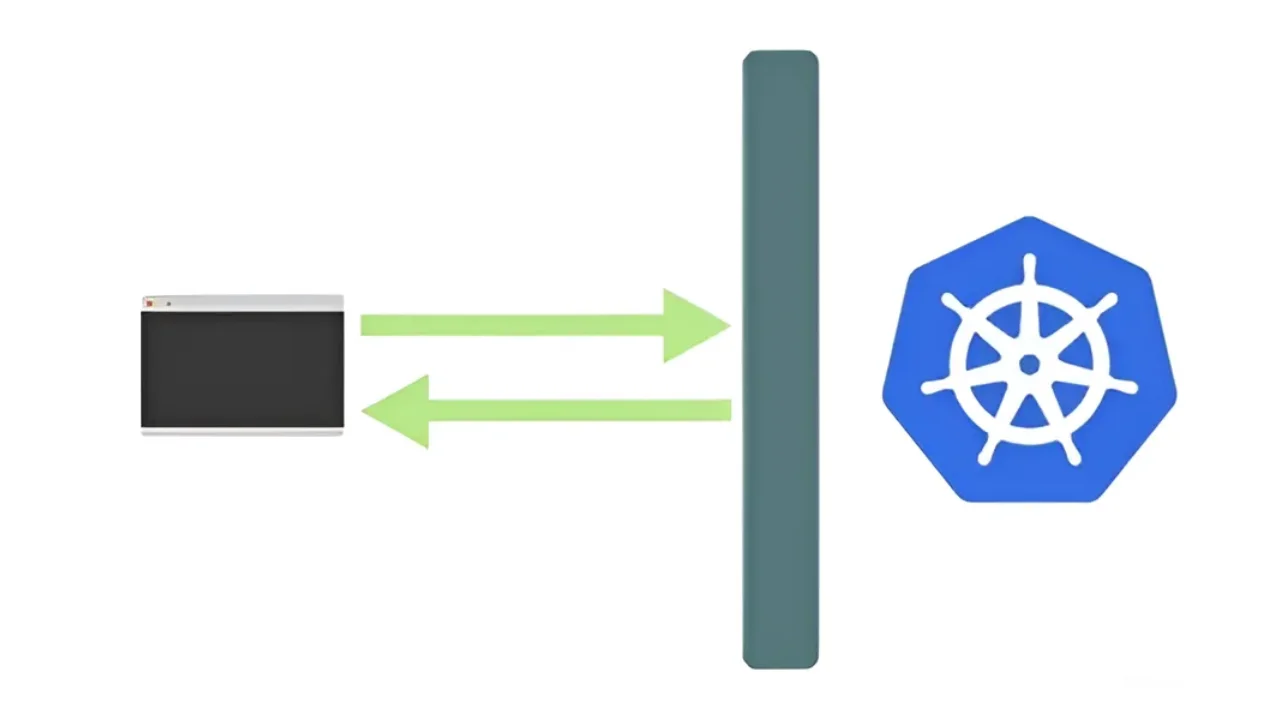
Kubernetes is just Linux
I started working with Kubernetes a couple of years ago. In the beginning this software looks as a huge technology made from scratch and is doing an extraordinary set of operations
DbGate: A Powerful Database Management Tool
DbGate is a versatile database management tool that caters to both SQL and NoSQL databases. As an open-source and free software, DbGate offers a comprehensive set of features to st
Mastering SQL: Comprehensive Guide To Structured Query Language
An in this article, we will discover in a high level the syntax and core features of the language that is actually used to bring the database schema design to existence... SQL. So.
What is OpenCart? Pros and Cons
The eCommerce platforms are often considered the “backbone” of any experienced business in the market. To embark on the eCommerce journey, your business needs to choose the rig
You Don’t Need a CSS Framework
Key Takeaways CSS frameworks offer short-term gains in speed and consistency but become increasingly hard to maintain over time. A codebase that uses a CSS framework will gradually
Is Your Container Image Really Distroless?
Containerization helped drastically improve the security of applications by providing engineers with greater control over the runtime environment of their applications. However, a